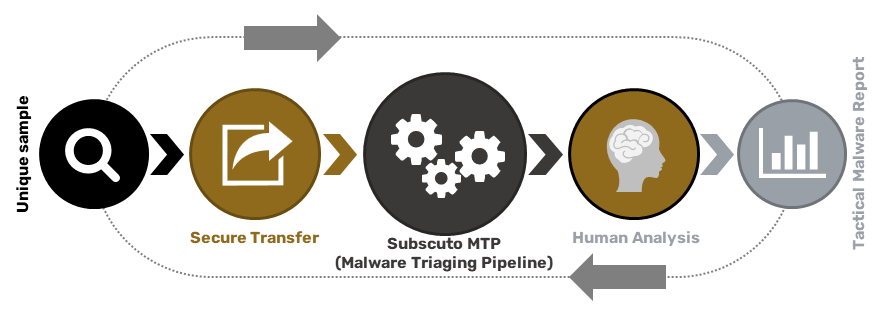
CHALLENGES OF FIGHTING AGAINST MALWARE IN MODERN SECURITY OPERATIONS
Analysis of suspicious code is inevitable at some point in the life of security teams. Numerous technologies, operating at network and endpoint levels, aid cyber security professionals in performing automated runtime analysis of code to conclude whether the code is benign or malicious.